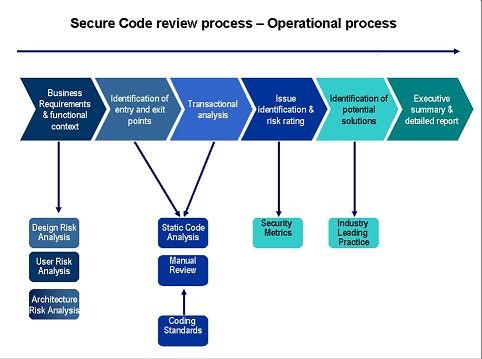
Step 1: Business Requirement and Functional content
Business requirements are the critical activities of an enterprise that must be performed to meet the organizational objective(s) while remaining solution independent. Functional requirements are very detailed and provide information on how business needs and goals will be delivered through a specific project. Below are the steps in this phase:
• Design Risk Analysis
• User Risk Analysis
• Architecture Risk analysis
Step 2:
I. Identification of entry and exit points
Identifying entry points and exit points to see where a potential attacker could interact with the application, identifying assets i.e. items/areas that the attacker would be interested in, and identifying trust levels which represent the access rights that the application will grant to external entities.
II. Transactional Analysis
It consists of the analysis of applications function to assert the presence of security controls that protect the confidentiality, integrity, availability and accountability of this functions. Below are the steps in this phase:
• Static code Analysis
• Manual Review
• Coding standards
Step 3: Issue Identification and Risk rating
The first step is to identify a security risk that needs to be rated. The tester needs to gather information about the threat agent involved, the attack that will be used, vulnerability involved in the code, and the impact of a successful exploit on the business. There may be multiple possible groups of attackers, or even multiple possible business impacts. In general, it’s best to err on the side of caution by using the worst-case option, as that will result in the highest overall risk. Risk rating is calculating an overall severity for the risk. This is done by figuring out whether the likelihood is low, medium, or high and then do the same for impact. Below is the phase involved i.e. Security Metrics
Step 4: Identification of potential solution
Identifying the solution to fix the vulnerabilities. Based on Industry leading practices tester should give remediation for the vulnerabilities.
Step 5: Executive summary and detailed report
An executive summary that provides a high-level view of vulnerabilities detected and even provides a security “score,” and a more detailed report that pinpoints which line of code looks troublesome and the vulnerability that was detected.