Application Security Tools And Security Testing Tools For Web Application Discovers security test is to find the vulnerabilities of the web application so the engineers can expel these vulnerabilities from the application and make the web application and information safe from any unapproved activity. And security testing tools to identify and measure the extent of security issues with your web applications
Web Application Security Assessment has become an unavoidable requirement for every organization. The risk factors for web applications are many and are continually growing day by day. Even a simple plugin like, old versions and application theme can lead to a breach of your organization’s data and potentially, internal network. Application security challenges should be addressed effectively in a timely manner.
Our security testing services scrutinizes the security loopholes in your application at various levels and reports the same to you. We are always there to fix those security loopholes for you to make sure your site is stable and runs smoothly without flaws.
Hackers crave for the annihilation of every organization’s reputation by breaching all their data’s and making them relinquish to their mettle, thus making them to flash in the news as the latest victim of cyber breach.
Web application security will be scrutinized by auditors due to a variety of factors like lack of developer’s education, rushed codes, going into production too soon, etc.
The benefits of having even just a single site tested can lead to a functional change in how the code is written and deployed, providing positive security change.
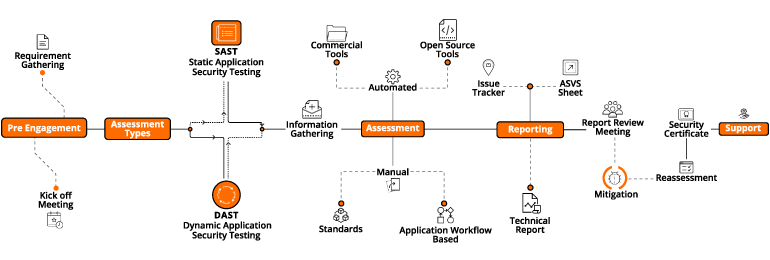
Because:
Apart from this:
