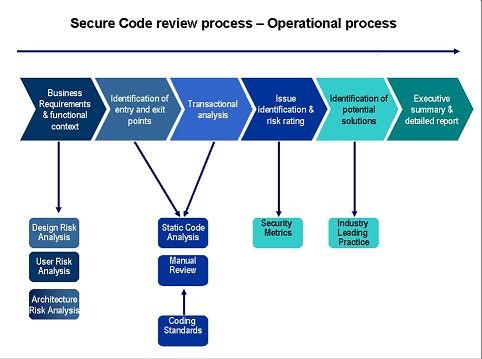
 Source code review Methodology
Source code review Methodology
Step 1: Business Requirement and Functional content
Business requirements are the critical activities of an enterprise that must be performed to meet the organizational objective(s) while remaining solution independent. …….
 LinkSoft become reseller for snappycode audit
LinkSoft become reseller for snappycode audit
As a professional software provider, Linksoft cooperates with global outstanding IT industries, reselling thousands of software includes Statistical Analysis, Development Program, Database Management, Network Security, Design and Edit software.
Linksoft cultivates its mature service along Commercial, Government, Academic and Home users, with more than 500,000 customers in Asia.
Read More● Data Validation – The most common web application security weakness is the failure to properly validate input from the client or environment. This weakness leads to almost all of the major vulnerabilities in applications, such as interpreter Injection, locale/Unicode attacks, file system attacks and buffer overflows. Data from the client should never be trusted for […]
Read More● Risks ● Purpose & Context – A payment web application will have higher security standards than a promotional website. ● Lines of Code – the more lines, the more bugs ● Programming Language – Unmanaged code → Chances of buffer overflow. ● Resources, Time & Deadlines. ● Automated tool for scanning the source code
Read MoreWhat is Static Code Review ? Code review is a systematic examination of source code with an intention to find and fix Vulnerability.Code reviews are primarily done during development phase to improve and secure the software or application. The cost of fixing the vulnerability after release to customer is nearly ten times the cost of […]
Read More1 ) Yet Another Static Code Analyzer (YASCA) YASCA is a static code analysis tool that can analyze php,java,C/C++ and javascript code for security vulnerabilities and code quality issues.One of the main advantages of this tool is that it can integrate other tools and plugins in order to scan many programming languages. YASCA runs through […]
Read MoreImportance of Automated Source Code Review Manual source code review is task that requires a lot of time and good understanding of the application source code that is being reviewed.So the use of automated static analysis tools is often necessary in order to help the security tester to identify the Vulnerabilities fast and more easily […]
Read MoreOWASP Top 10 Application Security Risks – 2017 A1:2017-Injection : Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization A2:2017-Broken Authentication Application functions […]
Read More1. Automation — Automation can save your time and energy which ultimately means you can invest your time and energy in some other aspects of development lifecycle, which will help you to release your software faster. 2. Security — Security is also one of the major concern and by adopting Static analysis tools you can cut the […]
Read MoreSource Code Analysis Tools In source code analysis tools, for the kinds of issues that can be identified during the product improvement stage itself, this is an amazing stage inside the advancement life cycle to utilize such instruments, as it gives quick input to the designer on issues they may be bringing into the code […]
Read More