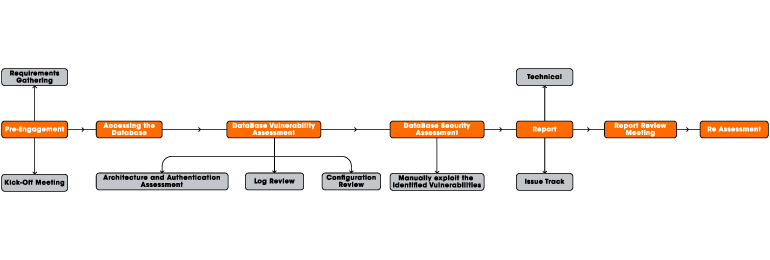
Snappy code audit’s Database Security Assessment is an integrated approach which provides systematic and proactive security to the database. Snappy code audit’s penetration testing eliminates the risk associated with both web and database specific attacks and supports compliance with relevant standards, laws & regulations. Leveraging an open-source or commercial database vulnerability assessment tool along with manual testing to discovers the known database security vulnerabilities. Snappy code audit’s database security testing is to prevent undesired information disclosure and data modification of data while ensuring the availability of the necessary service.
We are snappy audit tool we sell top rated updated security tool available in market and we provide open source instrument utilized for code audit and record survey by open source undertakings and organizations. Utilizing Review Board for code survey one can set aside extra cash and time. Survey Board can be incorporated with ClearCase, CVS, Perforce, Plastic etc
And Our Open Source Static Code Analysis which lets examination of C, accompanies a truly adaptable structure. Open source security examination apparatus for Java and C codes. PMD is an open source code analyzer for C/C++, Java, JavaScript. This is a basic device and can be utilized to discover regular defects.